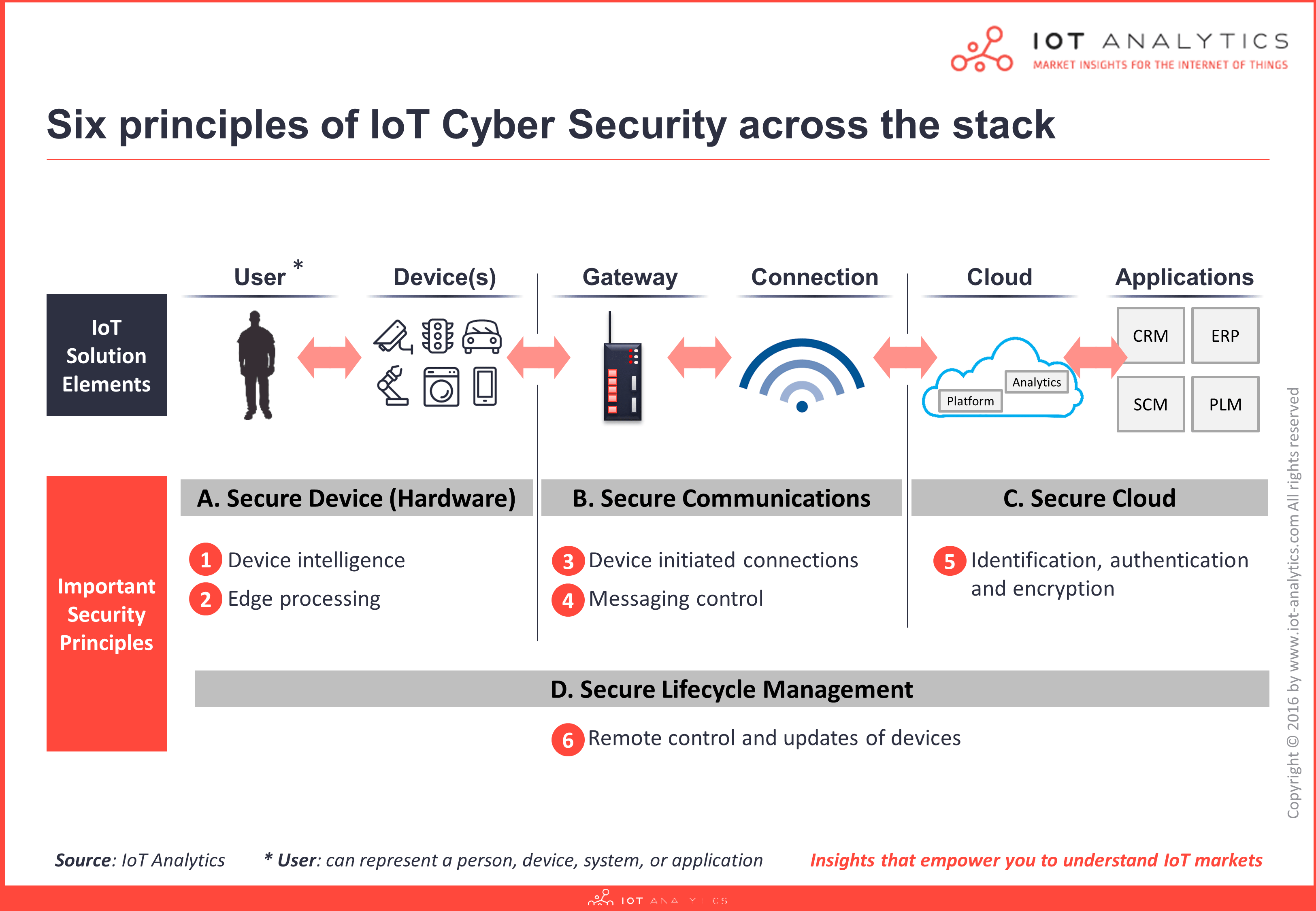
In Part 1 of this blog series Understanding IoT Security we looked at IoT cyber security architecture from a device and communication layer perspective. In this post, we shift our focus to the Cloud and Lifecycle Management, which present entirely different challenges and risks.
Even world leaders are starting to address the growing concerns of connecting billions of devices to the internet. The World Economic Forum recently commissioned a report to create a set of guidelines, designed for board-level use, that address the challenges and risks of cyber security in emerging markets based on hyper-connected technologies. Thus, IoT cyber security is high on the agenda for discussion in Davos, Switzerland this week.
However, as previously discussed, developing secure end-to-end IoT solutions requires a holistic approach that involves multiple levels and fuses together important security features across four layers: Device, Communications, Cloud, and Lifecycle Management. Again, George Cora, CEO of Ardexa is at hand to highlight key principles for IoT cyber security at the Cloud and Lifecycle Management layers:
C. Secure Cloud Layer
The cloud layer refers to the software backend of the IoT solution i.e., where data from devices is ingested, analysed and interpreted at scale to generate insights and perform actions. Security has always been a major topic of discussion when assessing the risk of using cloud versus on-premise solutions. However, for the Internet of Things cloud is viewed as a key enabler to widespread adoption. Cloud providers are expected to deliver secure and efficient cloud services by default, and protecting from major data breaches or solution downtime issues is becoming the norm.
Important IoT cyber security features:
- Sensitive information stored in the cloud (i.e., data at rest) must be encrypted to avoid being easily exposed to attacks e.g., when a compromised third party with lower security controls accesses your data for (say) advanced analytics operations.
- It is also beneficial to verify the integrity of other cloud platforms or third party applications that are trying to communicate with your cloud services to help protect against malicious activity.
- Digital certificates can play a key role for identification and authentication needs at the scale required for the IoT.
IoT Cyber Security Principles on the Cloud Layer:
5. Identification, authentication and encryption for machines … not humans
“People accessing cloud services will almost always use a password. In some cases, there may be two factor authentication such as a password plus a one-time password generator. Passwords are the accepted authentication method for humans to use. Machines however, are much better at handling digital certificates when accessing cloud services. Digital certificates use an asymmetric, encryption based, authentication system designed to not only authenticate a transaction, but also encrypt the channel from device to cloud before the authentication takes place. A digital certificate can also provide cryptographic identification that is very difficult to achieve with user-id/password.”
George Cora, CEO at Ardexa
D. Secure Lifecycle Management Layer:
Secure Lifecycle Management refers to an overarching layer with continuous processes required to keep the security of an IoT solution up-to-date i.e., ensuring sufficient security levels are in place from device manufacture, initial installation to the disposal of things. Security by design is only the first step in the ongoing effort to keep an IoT solution secure, further steps throughout the lifecycle include policy enforcement, regular auditing and vendor control. For more info contact us about our upcoming IoT security market report.
Important IoT cyber security features:
- Activity monitoring plays an important role to track, log and detect suspicious activity.
- IoT devices and applications need regular security patches in order to stay up-to-date, strengthen resistance against attack and fix possible vulnerabilities.
- Secure remote control is essential especially when maintaining billions of IoT devices.
IoT Cyber Security Principles on the Lifecycle Management Layer:
6. The security of remote control and updates
“Remote control, or the ability to send commands to a device throughout its lifecycle, can be a very sensitive, but powerful, feature. Remote control of a device is essential in allowing remote diagnostics, setting a new configuration, updating buggy software, retrieving files, resetting a machine learning algorithm with a new of set of learning data, adding new functionality to a product and more. The key to secure updates and remote control is to ensure that a device does not allow incoming connections (see principle 3), yet has a bi-directional connection, is correctly secured (see principle 1), uses a message switch as the communications channel (see principle 4) and is correctly implemented. Ultimately, the software on the device acts as a server, albeit one that only communicates with the cloud and does not allow anyone to connect. However, implementing remote control software and managing secure updates throughout the device lifecycle is tricky and not for everyone.”
George Cora, CEO at Ardexa
Real-world Examples
Silver-bullets rarely exist in addressing IoT security issues
Having presented several important IoT cyber security architecture features across four different layers and highlighted important principles, it is fair to say IoT security design is complex. Solutions to security will typically involve a number of key elements working together to minimise the various threats or exposures. This complexity is often ignored or mismanaged, in preference of more simplistic solutions. Recent real-life cases have demonstrated that solutions often require a broad range of approaches and considerations. The following examples demonstrate this very well.
Example 1: AFIT changes PLC firmware (Device Layer)
- In 2014, researchers with the U.S. Air Force Institute of Technology (AFIT) demonstrated the feasibility of booting an unsecure device with malicious firmware. They created a prototype rootkit that can sit undetected in the firmware of an industrial programmable logic controller (PLC) that enabled them to corrupt utility and plant floor operations in the factory.
Device Layer Solution Considerations:
Do equipment vendors provide rootkit malware protection?
Is the device vulnerable during installation?
Are devices regularly tested for malicious rootkits?
Does the IoT architecture enable remote testing of firmware?
Can regular service procedures of automation devices introduce vulnerabilities?
Can we detect rootkit malware problems?
George Cora, CEO at Ardexa
Example 2: Remote control of a car (Communication Layer)
- In 2015, two cybersecurity experts used a man-in-the-middle attack to take control over a Jeep on the freeway (e.g., controlling the air-conditioning, radio, windshield wipers and brakes). Although it was staged, the attack showed the potential for how dangerous man-in-the-middle attacks could be in theory and led to the recall of 1.4 million vehicles.
Communication Layer Solution Considerations:
Can we patch devices remotely
Does IoT architecture limit the damage of unauthorised intrusions?
Can third party testing play a role?
How should I protect against “edge” vulnerabilities?
Are there unintended linkages across segments of a large IoT system?
George Cora, CEO at Ardexa
Example 3: Unsecured customer data (Cloud Layer)
- In 2015, a UK based telecom and internet provider Talk Talk were subject to several cyber security breaches where customers’ data was exposed as it was stored unencrypted in the cloud. Hackers, were able to easily access and steal millions of customers’ credit card and bank details.
Communication Layer Solution Considerations:
When should data be stored on the device or the cloud?
Which data elements need encryption and to what level?
What types of firewalls are used in the IoT cloud?
Does the business have the correct culture to address IoT security risks?
George Cora, CEO at Ardexa
Example 4: Unsecure update process for a medical device (Lifecycle Management)
- In 2015, a hacker was able to raise the dosage limit on medication delivered to patients through a Hospira drug infusion pump. The main issue arose from an unsecure library update process and communication modules for the pumps.
Lifecycle Management Solution Considerations:
Can maintenance processes introduce new vulnerabilities?
Are access and privilege levels correct for an IoT implementation?
Are updates in software or firmware digitally signed or authenticated?
George Cora, CEO at Ardexa
Learning from such examples across the stack, and applying the six principles (laid out here and in Part 1 to real world solutions can make IoT devices and applications a lot easier to use, and much less likely to be compromised.
Stay tuned for Part 3 of our IoT cyber security blog series where we take a closer look at open architecture security in IoT and design considerations for the real world.
Find out more details about the 4 levels of IoT security architecture in our List of 150 IoT Security Companies and how the overall IoT security market is shaping up in our IoT Security Market Report released in September 2017.