
In short
- While industrial executives often cite AI and IT/OT convergence as the most promising future developments, these technologies create new and complex cyber attack surfaces.
- IoT Analytics’ 49-page OT Cybersecurity Insights Report 2026 identifies several trends related to IT/OT convergence and AI integration affecting OT security, with 5 discussed in this article:
1. The shift to hybrid (central-decentral) security architecture
2. The rise of zero trust microsegmentation
3. The enduring criticality of firewalls in IT/OT convergence
4. AI’s growing role in OT security
5. The new focus on securing AI workloads in OT
Why it matters
- For cybersecurity vendors: With OT cybersecurity increasing in importance, cybersecurity companies need to keep up with current trends and align their offerings accordingly to remain competitive.
- For enterprises: While IT/OT convergence and AI integration into OT come with many benefits, they also widen the cyber attack surface. Understanding current trends can help companies assess their cyber posture and consider appropriate OT cybersecurity solutions.
In this article
- OT cybersecurity’s increasing importance
- Foundational context: Understanding the Purdue Model of industrial control systems and OT security
- 5 key trends shaping OT cybersecurity
- Trend 1: The shift to hybrid (central-decentral) security architectures
- Trend 2: The rise of zero trust microsegmentation
- Trend 3: The enduring criticality of firewalls in IT/OT convergence
- Trend 4: AI’s growing role in OT security
- Trend 5: The new focus on securing AI workloads in OT
- Analyst opinion: The path forward in a converged, AI-driven world
- OT cybersecurity competitive landscape (Insights+ exclusive)
- Regulation- and architecture-related OT cybersecurity trends (Insights+ exclusive)
This article is derived from it-sa 2025, a major cybersecurity conference.
Get insights from the world’s leading industrial technology exhibitions 2026
Full it-sa conference coverage is available to IoT Analytics corporate subscribers. Throughout 2026, subscribers will receive 10 post-conference reports from major industrial technology fairs, including Hannover Messe, SPS, and Automate.
Corporate subscription access includes:
- 10 comprehensive post-conference write-ups
- Key market numbers and market reports
- Analysis of trends, vendor strategies, and more
Already a subscriber? View your reports and trackers here →
OT cybersecurity’s increasing importance
The most promising upcoming technologies introduce unpredictable cybersecurity risks. Industrial AI and the accelerating convergence of IT and OT systems are currently cited by industrial executives as the most promising future developments. In fact, 44% of manufacturing CEOs discussed their AI initiatives in Q4 2025 earnings calls (up 35% YoY), touting its enormous impact.
Key CEO quote on AI integration
“Our AI-powered tool, the Cookbook, provides employees access to 150 years of company knowledge on ketchup production and is leading to more efficient operation.”
Carlos Abrams-Rivera, CEO, Kraft Heinz (source)
Quotes like the above show that executives clearly see the benefits, with AI and IT/OT convergence promising to address the industry’s most pressing concerns, including improving operational efficiency, countering skill shortages, and enabling true real-time operational visibility. However, those 2 technologies also create new and complex attack surfaces that legacy OT security models were not designed to handle.
Ransomware and hacktivist attacks on OT assets rising. In June 2025, US-based technology and manufacturing conglomerate Honeywell reported that in Q1 2025 alone, there were over 2,400 ransomware attacks (a sharp upward trend compared to the 6,130 such incidents in 2024 overall), with the OT layer being the prime target. Vulnerable OT security has also become a target for state-aligned hacktivists, according to the US’ Cybersecurity & Infrastructure Security Agency (CISA): in 2023, hacktivists associated with Iran’s Islamic Revolutionary Guard Corps reportedly targeted PLCs and HMIs from Israeli-based companies, and in 2024, the agency reported that pro-Russian hacktivists were targeting outdated virtual network computing software and weak or default passwords. In December 2025, CISA released guidance on the secure integration of AI in OT, highlighting OT-specific failure modes such as model drift and safety process bypasses.
Increasing focus on OT security. OT cyber threats and attacks like the above, along with the growing number of cybersecurity regulations worldwide to mitigate cyber threats to data and national infrastructure, have made OT security a top cybersecurity topic. Some cybersecurity companies have placed a specific focus on OT security, such as US-based Dragos, and technology giants like Microsoft have dedicated a portion of their security blog to IoT and OT security and threat intelligence.
Additionally, while on the ground at the it-sa Expo&Congress (Europe’s biggest IT security conference held in Nürnberg, Germany) in October 2025, a team of IoT Analytics analysts observed numerous critical infrastructure and industrial security showcases, with industrial automation or cybersecurity companies like Siemens (from Germany), Palo Alto (US), CrowdStrike (US), Fortinet (US), and Checkpoint (Israel) having the largest exhibitions dedicated to OT security.
Report on the current state of OT cybersecurity. Based on observations and interviews at it-sa 2025, along with research on cybersecurity regulations, architecture, and vendor offerings, the team published the 49-page OT Cybersecurity Insights Report 2026 (published December 2025). The report delves into 10 OT cybersecurity trends, 5 of which are related to IT/OT convergence and AI and are shared below.
This year’s [it-sa] made one thing clear: OT security is no longer a niche issue. It’s becoming a strategic pillar for ensuring operational continuity, compliance, and trust across industries and critical infrastructures.
Italy-based IT consulting and system integration company Reply (via LinkedIn)
Foundational context: Understanding the Purdue Model of industrial control systems and OT security
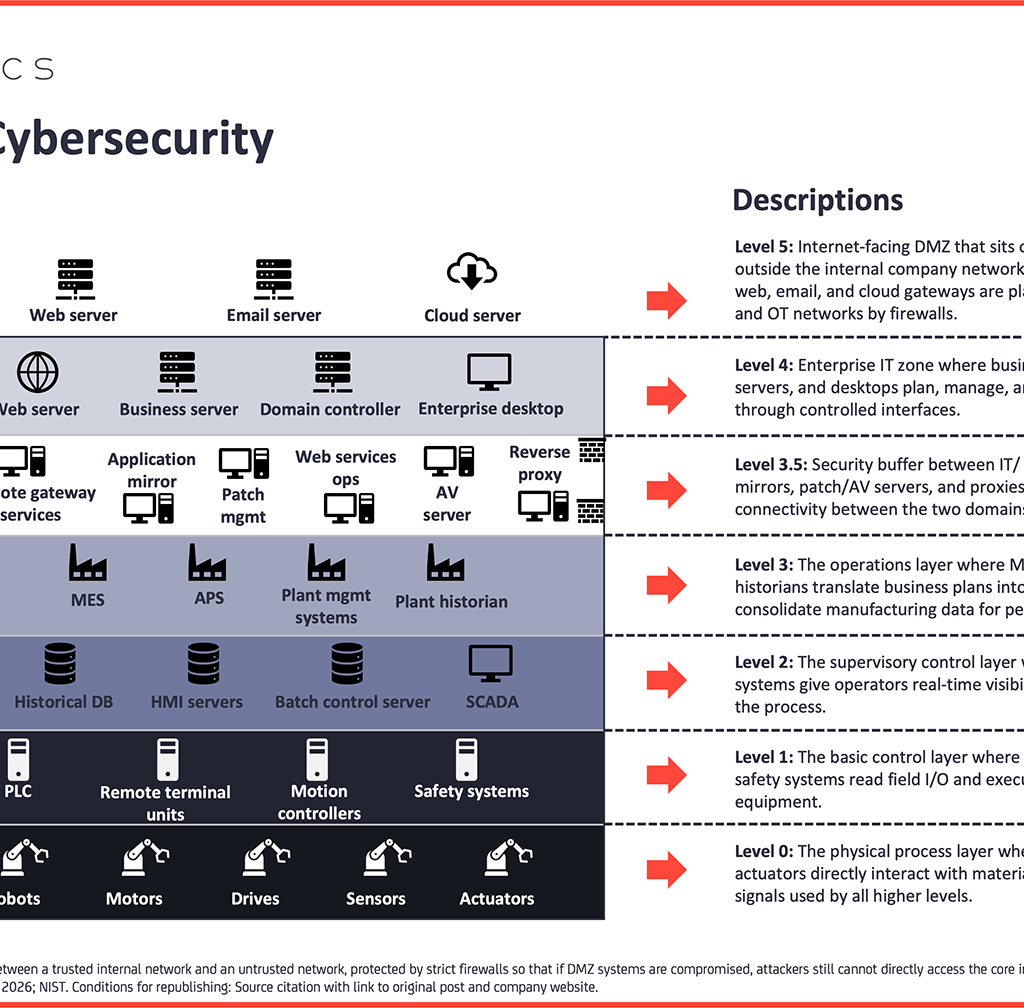
The Purdue Model is the long-standing architectural framework for industrial control systems (ICSs). The model segments the industrial network into distinct hierarchical levels, creating a logical separation between enterprise (IT) and operational (OT) functions.
The distinct levels of the model are as follows:
- Level 0: Physical process/field level – Where robots, motors, sensors, and actuators directly interact with physical processes.
- Level 1: Basic control – Where PLCs, remote terminal units, and safety systems execute deterministic control logic to drive equipment.
- Level 2: Supervisory control – Where SCADA and HMI systems provide operators with real-time visibility and high-level process control.
- Level 3: Operations systems – The manufacturing management layer, where systems like manufacturing execution systems and plant historians translate business plans into production execution.
- Level 3.5: The “demilitarized zone” (DMZ) between IT/OT – A critical security buffer that controls data flow between the IT and OT domains.
- Level 4: Enterprise zone – The corporate IT network where business applications like ERP and business servers reside.
- Level 5: Internet-facing DMZ – The public-facing network infrastructure, hosting services like web and email servers.
In the context of IT/OT convergence, Level 3.5 (the IT/OT DMZ) acts as a controlled buffer, allowing necessary data to flow between business and plant systems without creating a flat, insecure network.
5 key trends shaping OT cybersecurity

Trend 1: The shift to hybrid (central-decentral) security architectures
Hybrid security designs improving resilience and oversight. Industrial organizations are moving away from monolithic security models toward more resilient hybrid designs. This approach is essential for modern industrial environments that mix legacy, air-gapped equipment with new, connected systems. It combines the strengths of centralized, cloud-based visibility for broad threat detection with the necessity of decentralized, on-site protection for operational integrity.
The dual benefit of a hybrid model is its ability to provide both comprehensive oversight and localized resilience. Centralized analytics can correlate data from across IT and OT networks, enabling the detection of sophisticated, cross-domain attacks. Simultaneously, decentralized controls (such as endpoint protection and local network segmentation) ensure that critical processes remain safe and operational, even if connectivity to the central cloud is lost.
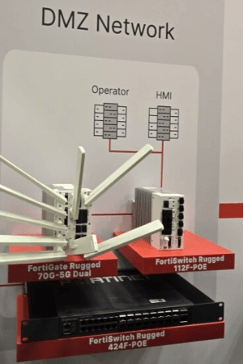
Example: Fortinet’s OT Security Platform
US-based cybersecurity and networking company Fortinet’s OT Security Platform (last updated in March 2025) uses a hybrid model that combines centralized oversight with local protection. Local firewalls and microsegmentation isolate assets to prevent lateral movement and contain incidents. The platform also integrates FortiGate next-generation firewalls as its core enforcement layer, paired with FortiSwitch. In this setup, the company says the devices can segment and secure traffic between enterprise IT networks and industrial systems, helping protect assets such as PLCs and HMIs.
Trend 2: The rise of zero trust microsegmentation
Zero trust (ZT) microsegmentation reducing legacy system risk. ZT microsegmentation is rapidly becoming a cornerstone of modern OT security. It is a dynamic, software-defined approach that moves beyond traditional static network perimeters by creating logically defined communication boundaries around critical assets. It is particularly vital for protecting legacy and unpatchable devices, where vulnerabilities cannot be fixed through conventional updates. Instead of relying solely on patching, organizations are logically enforcing who and what is allowed to communicate, drastically reducing the attack surface.
“[Z]ero trust was everywhere [at it-sa 2025]. Everywhere I looked, somebody was talking about zero trust.”
Dr. Patrick Jauernig, co-founder at Sanctuary Insights (IoT Analytics interview at it-sa)
Example: Siemens SINEC Secure Connect platform
Germany-based industrial automation company Siemens’ SINEC Secure Connect platform (launched in October 2025) creates a virtual overlay network on top of the existing physical infrastructure, physical wiring and topology remain unchanged. This allows security teams to define and enforce granular policy controls (e.g., restricting access by device, application, or data flow) without altering the underlying network. By creating these micro-segments, the company says the platform directly addresses a primary OT security goal: reducing lateral movement within the plant and making it nearly impossible for attackers to move from a compromised system to other critical assets.
Trend 3: The enduring criticality of firewalls in IT/OT convergence
Industrial firewalls enforcing segmentation and OT protocol control. Firewalls remain a critical control layer, especially at the IT/OT convergence point located at Level 3.5 of the Purdue Model. Their function has evolved beyond being simple barriers; modern industrial firewalls have become sophisticated tools for network segmentation, deep packet inspection of OT-specific protocols like Modbus and Profinet, and policy enforcement within a ZT framework.
These firewalls serve a multifaceted role, establishing isolation zones that strictly control traffic between enterprise and industrial networks, preventing unauthorized lateral movement. They are also essential for preventing operational disruptions.
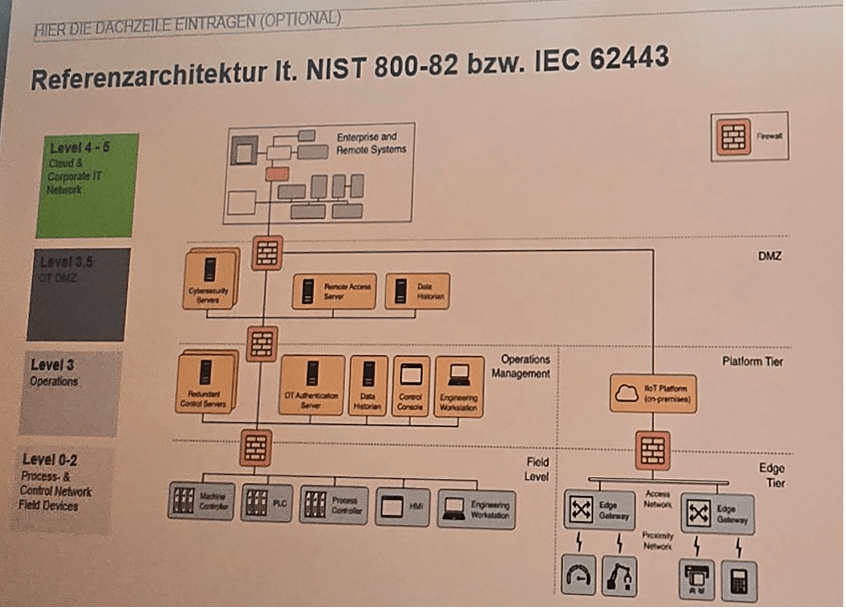
Example: Cancom NIST- and IEC-aligned firewall reference architecture
At it-sa 2025, Germany-based hybrid IT services provider Cancom demonstrated how layered firewalls enforce compliant data flow across OT architectures. In its reference model shown below, the primary firewall sits between Level 4–5 (cloud and corporate IT) and Level 3.5 (OT DMZ) to ensure only validated, policy-compliant data enters OT systems. Additional firewalls segment deeper layers, including edge and field devices, aligning with standards such as NIST 800-82 and IEC 62443.
Trend 4: AI’s growing role in OT security
AI streamlining OT anomaly detection and response. AI is becoming a core component in OT security workflows, appreciated for its ability to help cut through the noise of countless alerts, accelerate incident investigations, and correlate subtle events across the IT/OT boundary. AI-powered tools are helping overburdened security teams by automating the analysis of complex data streams from both the factory floor and the enterprise network.
The primary applications of AI in OT security include:
- Profiling network behavior to baseline normal operations and instantly flag unusual or unauthorized device actions
- Correlating plant-level data with broader IT security signals to reduce blind spots and identify attacks that traverse both domains
- Guiding operators through response procedures with AI assistants that can interpret alerts, suggest root causes, and recommend safe, production-aware actions
Example: CrowdStrike’s Charlotte AI
US-based cybersecurity company CrowdStrike deploys lightweight agents down to Purdue Level 2 and combines them with cautious network probing for lower-level devices. Telemetry is funneled into its Enterprise Graph and processed by Charlotte AI, which provides agentic responses to triage alerts, assess exploitability, and recommend next actions. The philosophy is to “collect once, reuse, recycle” data across endpoint detection and response, vulnerability management, and attack-path analysis.
Trend 5: The new focus on securing AI workloads in OT
AI-driven operations requiring model-level security controls. As AI models are deployed closer to physical processes, a new security paradigm is emerging: protecting the AI workloads themselves. When AI begins to influence or automate operational decisions, the security perimeter must expand to govern the AI models, their training data, and the autonomous actions they are permitted to take. An unsecured AI system in an OT environment presents significant operational and safety risks.
Key threats include data poisoning, where an attacker manipulates input data to corrupt a model’s output, and model misuse, where a compromised AI could trigger unsafe actions. This shift requires a new way of thinking about security controls, moving from protecting systems from threats to governing the rights and permissions of an intelligent agent.
“The overall vision is that AI will take over more and more tasks, and AI will do a lot of work. In that sense, we have to treat AI like a person: in the future, AI will need security permissions and rights to perform actions, and we will need to control what it is allowed to do.”
Representative at Cisco (IoT Analytics interview at it-sa)
Analyst opinion: The path forward in a converged, AI-driven world
IoT Analytics Principal Analyst Satyajit Sinha and Analyst Justina Sava attended the it-sa Expo&Conference in October 2025, observing the latest cybersecurity trends and meeting with experts in the field.
Based on the findings in the OT Cybersecurity Insights Report 2026, the team believes the convergence of IT and OT and the integration of AI in OT have required a fundamental rethinking of industrial security by vendors and industrial enterprises alike. The 5 trends above represent more than a technological evolution; they are a mandate for a fundamental shift away from static, perimeter-based defenses and toward a more dynamic, intelligent, and layered security posture. The future of OT security lies in hybrid architectures that balance central visibility with local resilience, enforce granular control through ZT principles, and leverage AI to both defend the network and secure its own operational role.
Alongside these powerful technological shifts, the report identifies 5 additional trends related to regulations and architecture that are impacting how vendors approach OT security. Regulatory drivers such as Europe’s Network and Information Security 2 (NIS2) Directive and Cyber Resilience Act are compelling organizations to elevate cybersecurity maturity from an operational task to a board-level priority, creating a new standard for industrial resilience. Meanwhile, as OT has several messaging protocol layers below the standard Internet protocol layer of IT, vendors are working to extend OT security down to the serial and analog layers to capture relevant data for real-time security monitoring.
OT cybersecurity competitive landscape (Insights+)
Access key market data for $99/month per user
The Insights+ Subscription unlocks exclusive facts & figures. You will gain access to:
- Additional analyses derived directly from our reports, databases, and trackers
- An extended version of each research article not available to the public
Full report access not included. For enterprise offerings, please contact sales: sales@iot-analytics.com
Disclosure
Companies mentioned in this article—along with their products—are used as examples to showcase market developments. No company paid or received preferential treatment in this article, and it is at the discretion of the analyst to select which examples are used. IoT Analytics makes efforts to vary the companies and products mentioned to help shine attention on the numerous IoT and related technology market players.
It is worth noting that IoT Analytics may have commercial relationships with some companies mentioned in its articles, as some companies license IoT Analytics market research. However, for confidentiality, IoT Analytics cannot disclose individual relationships. Please contact compliance@iot-analytics.com for any questions or concerns on this front.
More information and further reading
Sign up for our research newsletter and follow us on LinkedIn to stay up-to-date on the latest trends shaping the IoT markets. For complete enterprise IoT coverage with access to all of IoT Analytics’ paid content & reports, including dedicated analyst time, check out the Enterprise subscription.
Already a customer?
Read the full OT Cybersecurity Insights Report 2026
A 49-page report analyzing key trends in OT cybersecurity– based on observations and interviews at IT-SA 2025, Europe’s largest cybersecurity conference and exhibition.


