

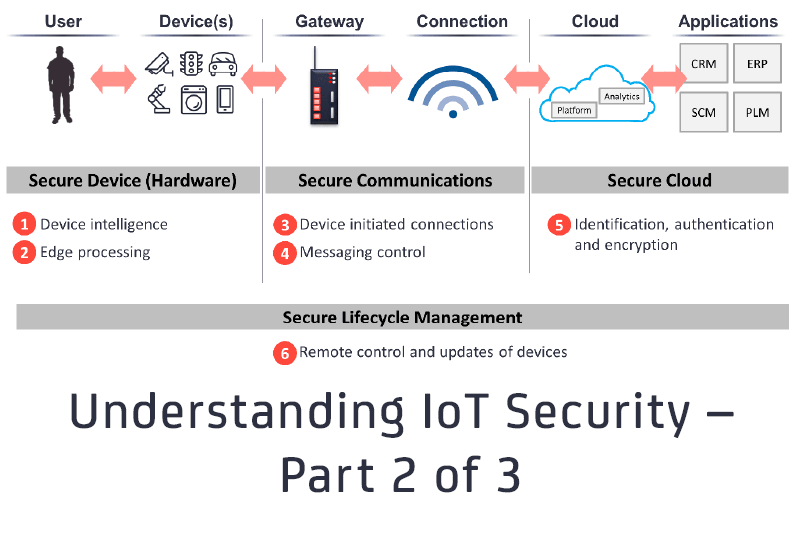
Understanding IoT Security – Part 2 of 3: IoT Cyber Security for Cloud and Lifecycle Management
In Part 1 of this blog series Understanding IoT Security we looked at IoT cyber security architecture from a device and communication layer perspective. In this post, we shift our focus to the Cloud and Lifecycle Management, which present entirely different challenges...
IoT 2016 in review: The 8 most relevant IoT developments of the year
As we go into 2017 our IoT Analytics team is again evaluating the main IoT developments of the past year in the global “Internet of Things” arena. This article highlights some general IoT 2016 observations as well as our top 8 news stories, with a preview for the...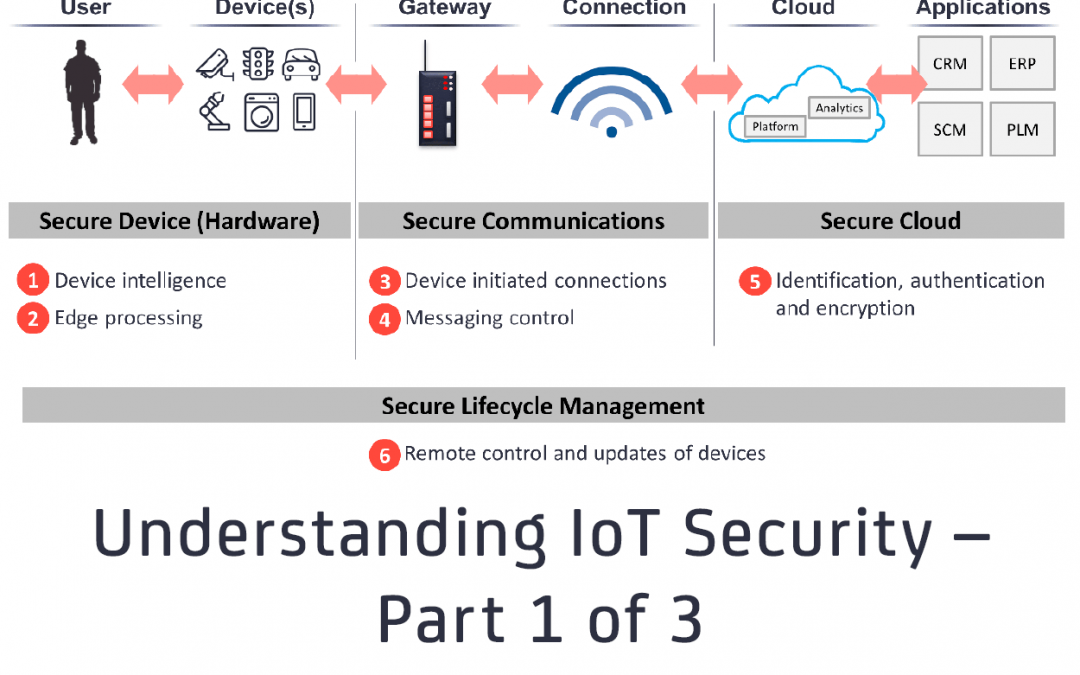
Understanding IoT Security – Part 1 of 3: IoT Security Architecture on the Device and Communication Layers
The massive scale of recent DDoS attacks (October 2016) on DYN’s servers that brought down many popular online services in the US, gives us just a glimpse of what is possible when attackers are able to leverage up to 150,000 unsecure IoT devices as malicious...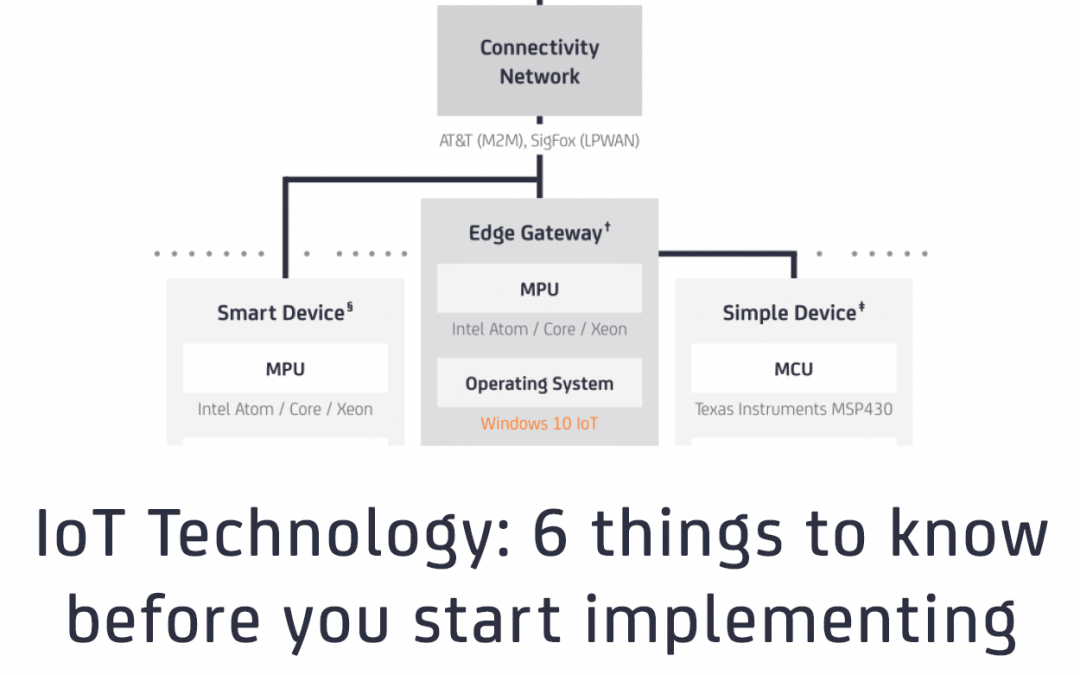
Implementing IoT technology: 6 things to know before you start
As we close out 2016 implementing IoT technology still remains a challenge for most manufacturers looking to digitize their products or services. Our research suggests that by the end of 2016 we will surpass 10,000 global enterprise IoT projects. While most of them...
