Description
Enterprise Cybersecurity Adoption Report 2021
The Enterprise Cybersecurity Adoption Report 2021 is part of IoT Analytics’ ongoing coverage of IoT software & platforms (IoT Platforms/Software Research Workstream).
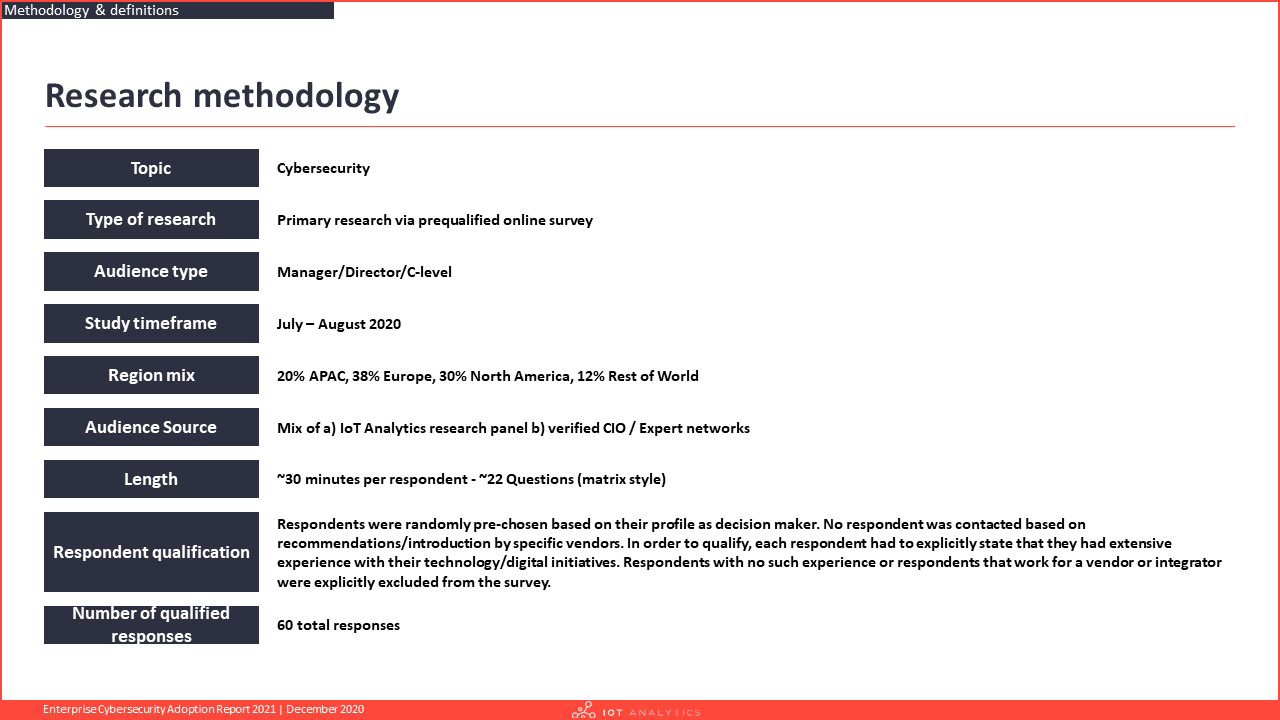
The information presented in this report is based on an extensive survey, with leading cybersecurity decision-makers among manufacturing and other industries. The purpose is to inform other market participants about the current state of cybersecurity threats and adoption of cybersecurity tools across companies.
Survey participants were randomly selected, and their knowledge independently verified. In order to ensure complete objectivity, IoT Analytics did not alter or supplement any survey results and also did NOT accept any participation from participants that were suggested from third-parties (e.g., customers of specific vendors).
Related reading:
IoT Analytics published a blog post on “The leading enterprise cybersecurity companies 2021” which is derived from the report which can be viewed here.
Find out:
- What cybersecurity threats are seen as most risky?
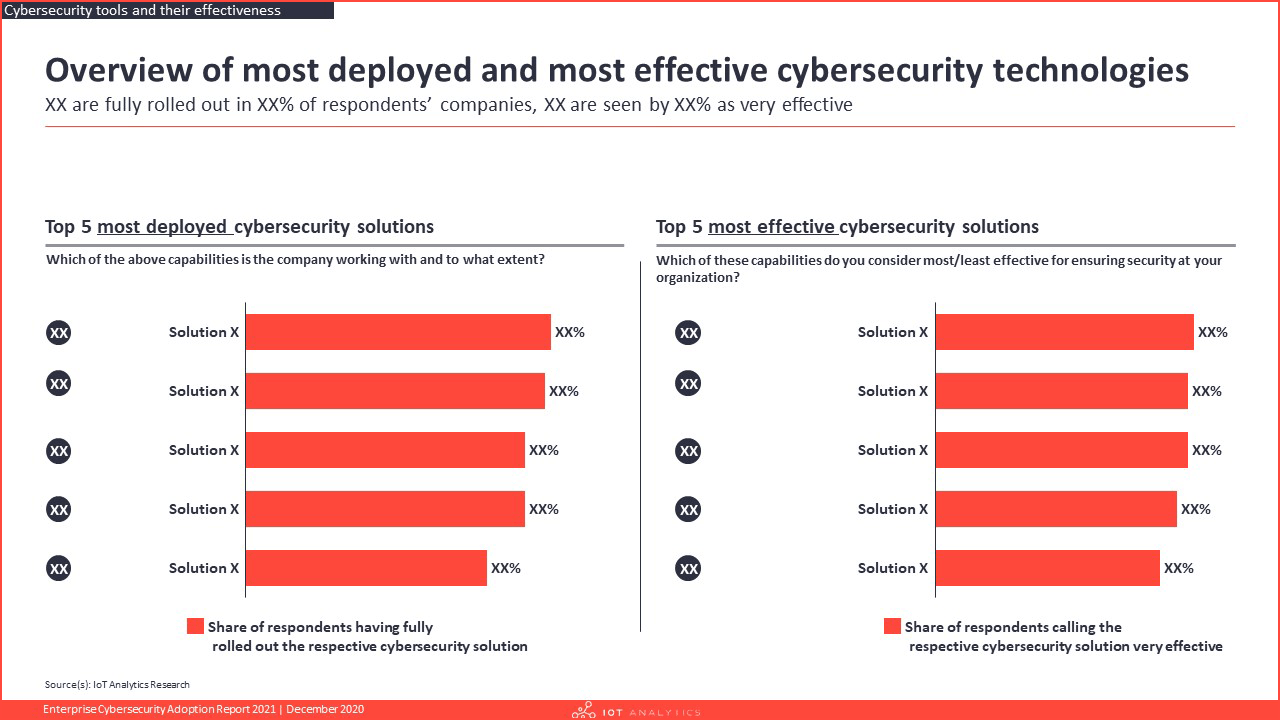
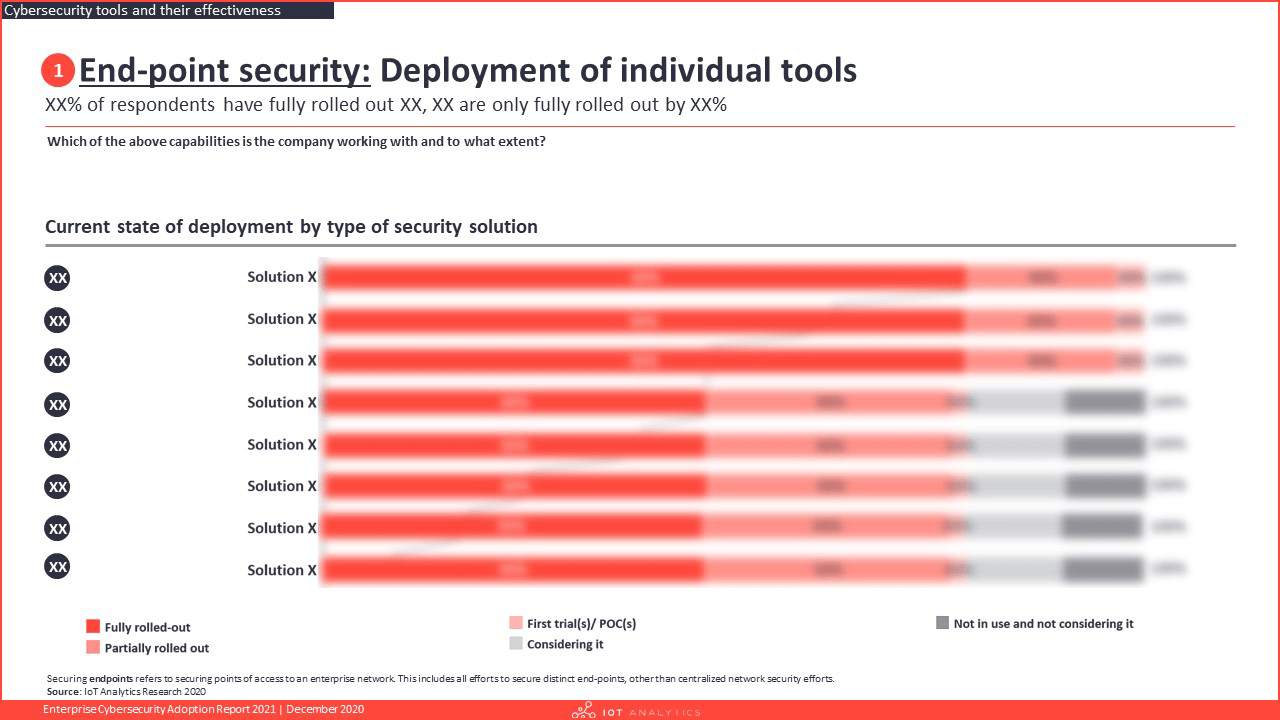
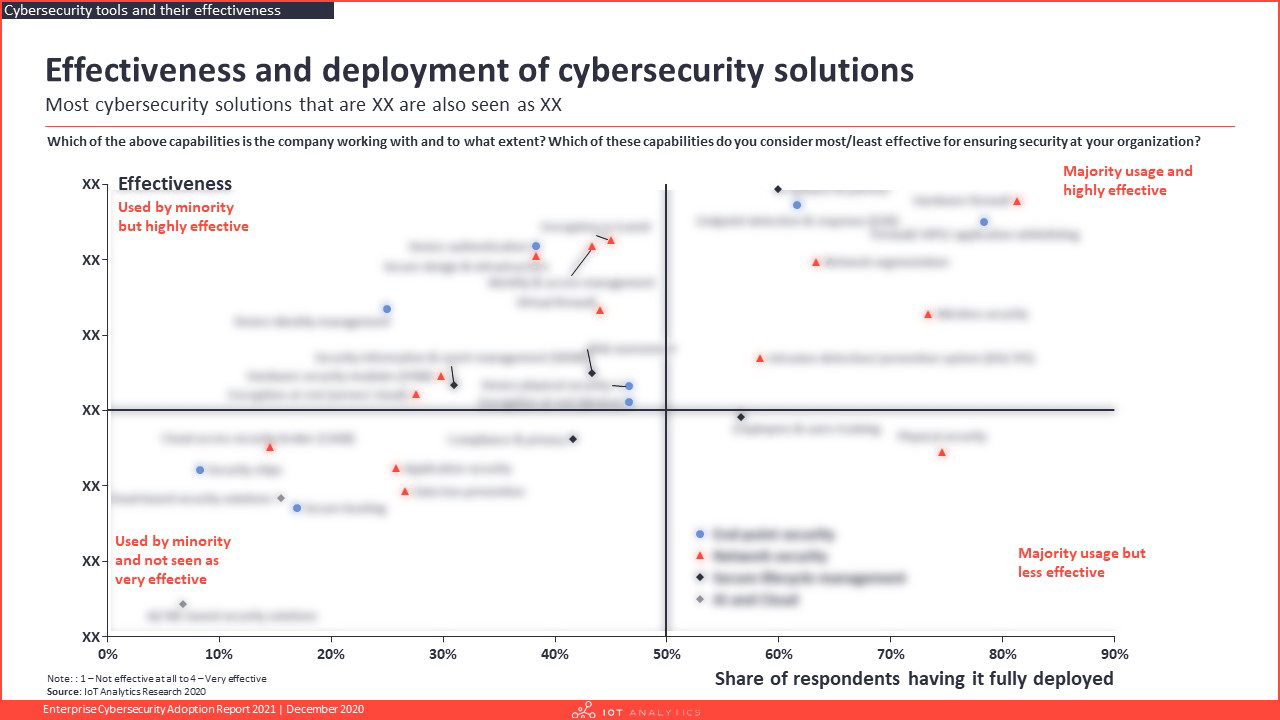
- What cybersecurity solutions are companies adopting and to which degree?
- Which cybersecurity tools are seen as most effective?
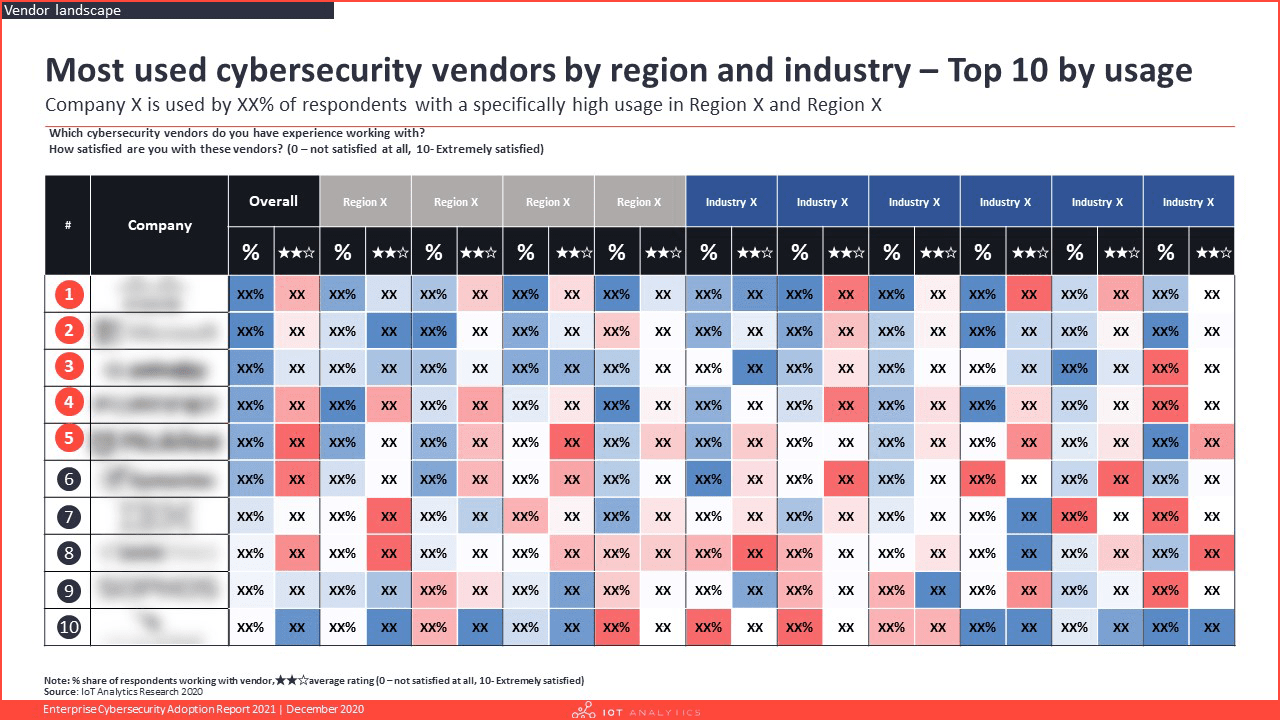
- Which are some of the common cybersecurity vendors and how well-perceived are they?
- Who is deciding and influencing the purchase of cybersecurity products and services?
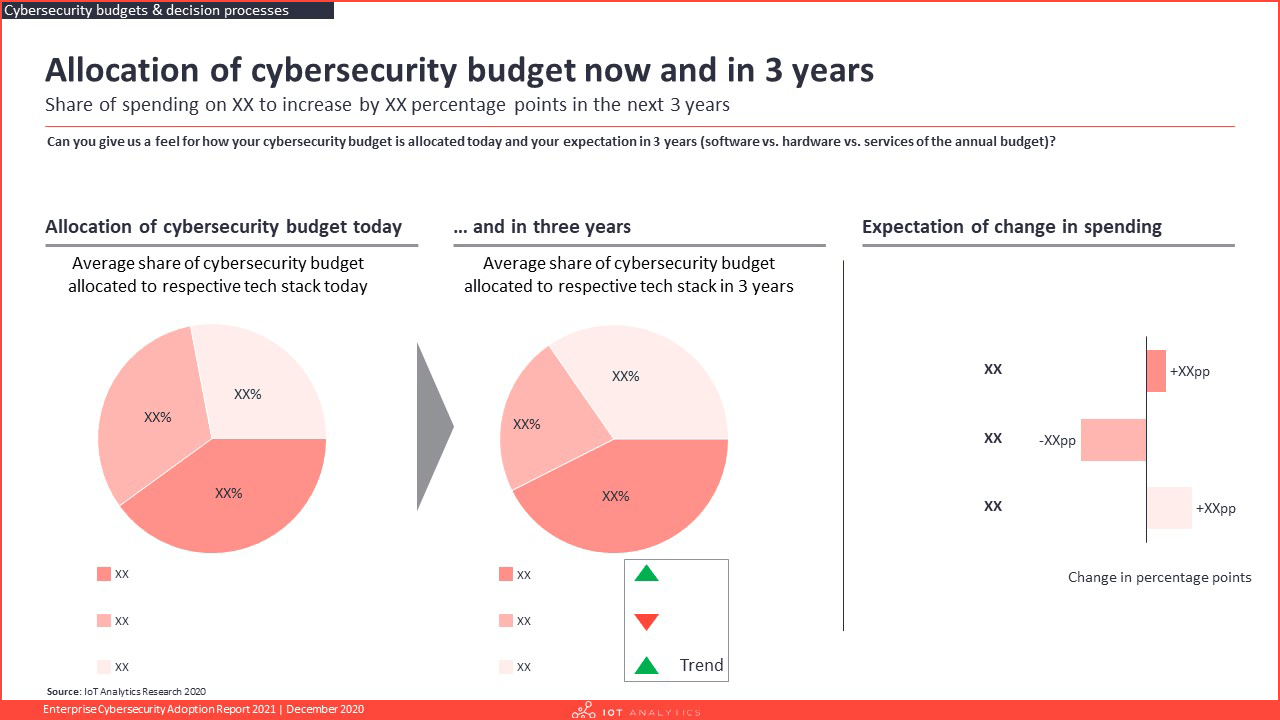
- How is the spending distributed across the tech stack?
- Which regions are preferred to host servers with cybersecurity related data or software?
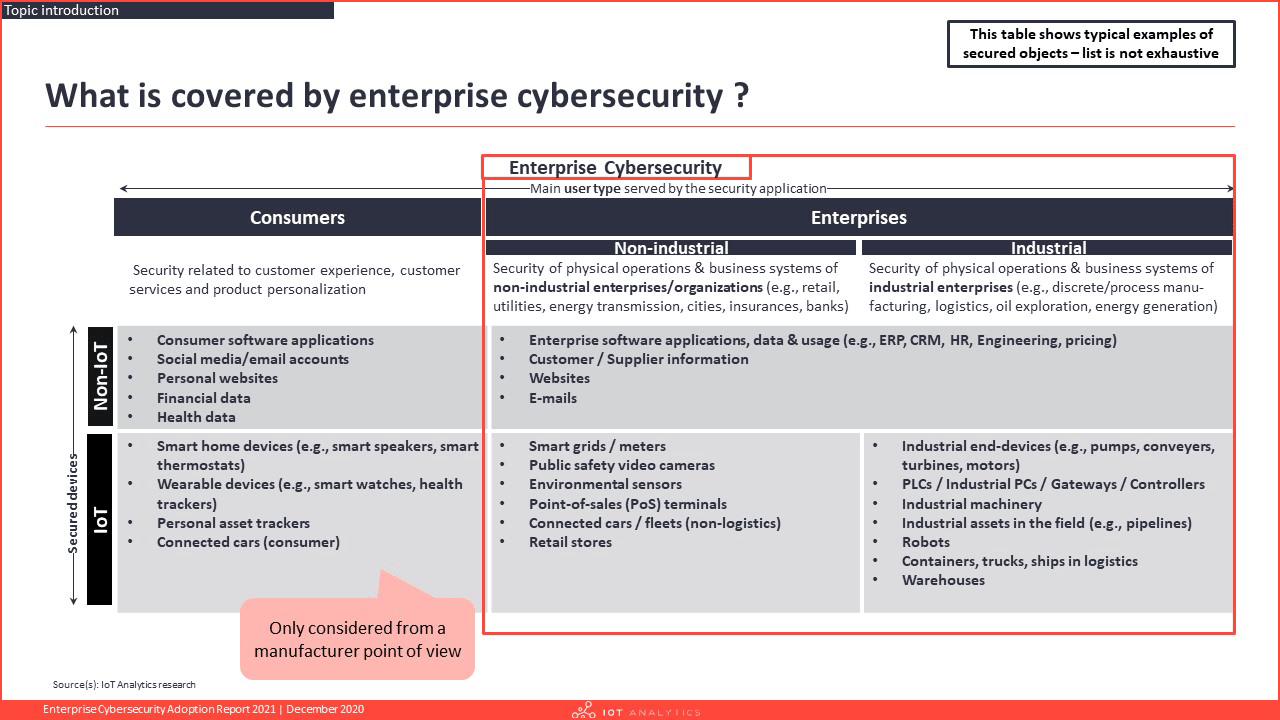
- How do companies secure their operations?
- How do companies secure their connected product?
- How has COVID-19 impacted the cybersecurity situation?
- What are best-practices of mitigating IoT security risks?
Available pricing plans:
See Terms & Conditions for license details.
Single User License
120 page PDF- 1 named user (in your organization within the country of purchase)
- Complete adoption report in PDF
- Complete adoption report in PPT
Team User License
120 page PDF- 1-5 named users (in your organization within the country of purchase)
- Complete adoption report in PDF
- Complete adoption report in PPT
Enterprise Premium License
120 page PDF + PPT- Report may be distributed to all employees of the enterprise
- Complete adoption report in PDF
- Complete adoption report in PPT
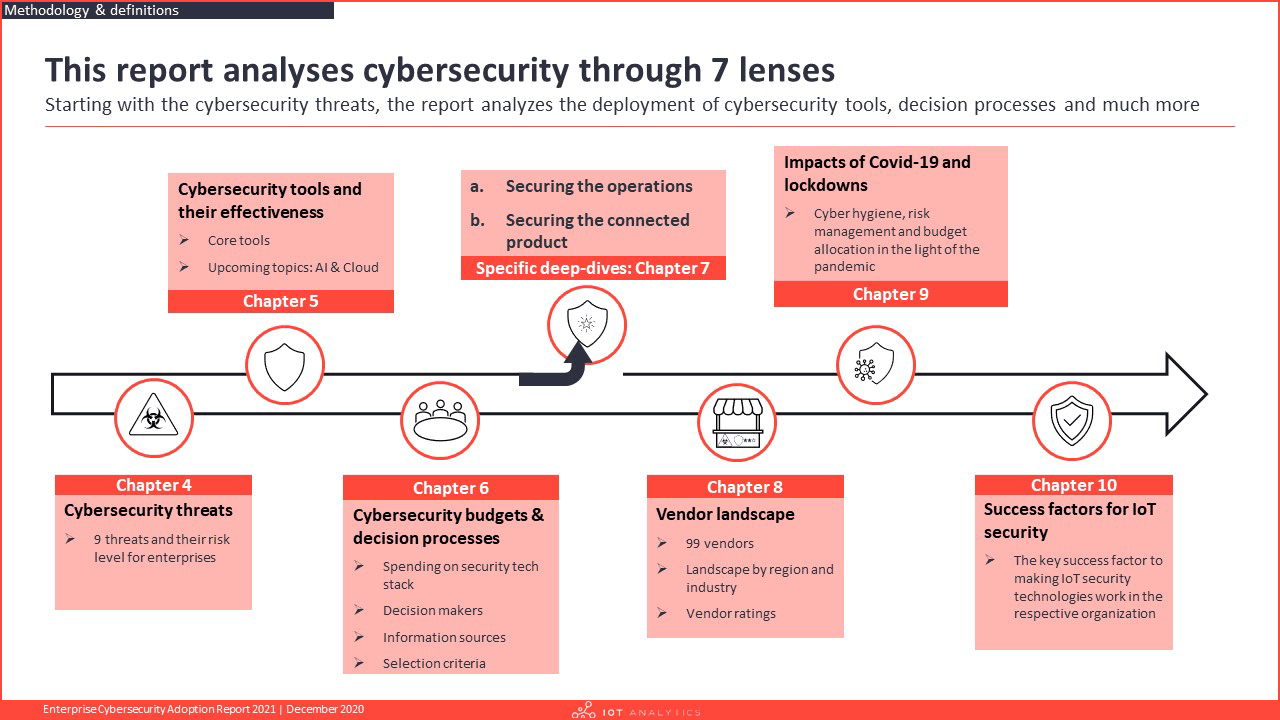
At a glance:
- Cybersecurity threats
- Cybersecurity tools and their effectiveness
- Cybersecurity budgets & decision processes
- Specific deep-dives
- Vendor landscape
- Impact of COVID-19 and lockdowns
- Success factors for IoT security
Companies mentioned in the report:
Cisco, Microsoft, Palo Alto Networks, Fortinet, McAfee, Symantec, IBM, Darktrace and 91 more.
Sample:
Request a sample of the report: