Description
As the Internet of Things (IoT) begins to transform businesses, economies and society, IoT security is emerging as an integral element that must be considered in the overall IoT infrastructure.
New threats emerge as billions of devices are being connected to the internet. The unprecedented scale of recent DDoS attacks (Mirai) and Ransomware attacks (WannaCry) gave us just a glimpse of what is possible when attackers leverage thousands of unsecure IoT devices as malicious endpoints.
This report aims to give deep insights into the complex IoT security market, showcase some innovative approaches that tackle the main challenges, and highlight key findings.
Find out:
- How the global IoT security market will develop from 2017 to 2022
- How the IoT security market breaks down across 12 industries
- How the regional split of the IoT security market will develop
- Which firm is leading the IoT security market
- Which are the top 10 firms in the global IoT security
- How 10 large firms and 5 innovative smaller firms tackle IoT security
- Which solution type (software, hardware, services) will dominate the market
- What are the 4 layers and 21 technology areas of IoT security
- How 8 companies implemented IoT security in real-world implementations
- What the 5 key implementation considerations for developing secure IoT solutions are
- What the 6 main trends shaping the IoT security market are
- Which 150 companies are tackling the challenges of IoT security
Available pricing plans:
See Terms & Conditions for license details.
Single User License
50% off- 1 Named user (in your organization within the country of purchase)
- Complete market report in PDF
- 4 Data tables for the market model
- Bonus: 2017 List of 150 IoT Security Companies
- 1 Hour dedicated analyst discussion
Team User License
50% off- 1-5 Named users (in your organization within the country of purchase)
- Complete market report in PDF
- 4 Data tables for the market model
- Bonus: 2017 List of 150 IoT Security Companies
- 1 Hour dedicated analyst discussion
Enterprise Premium License
50% off- Unlimited users (in your organization within the country of purchase)
- Complete market report in PDF
- 4 Data tables for the market model
- Bonus: 2017 List of 150 IoT Security Companies
- 1 Hour dedicated analyst discussion
At a glance:
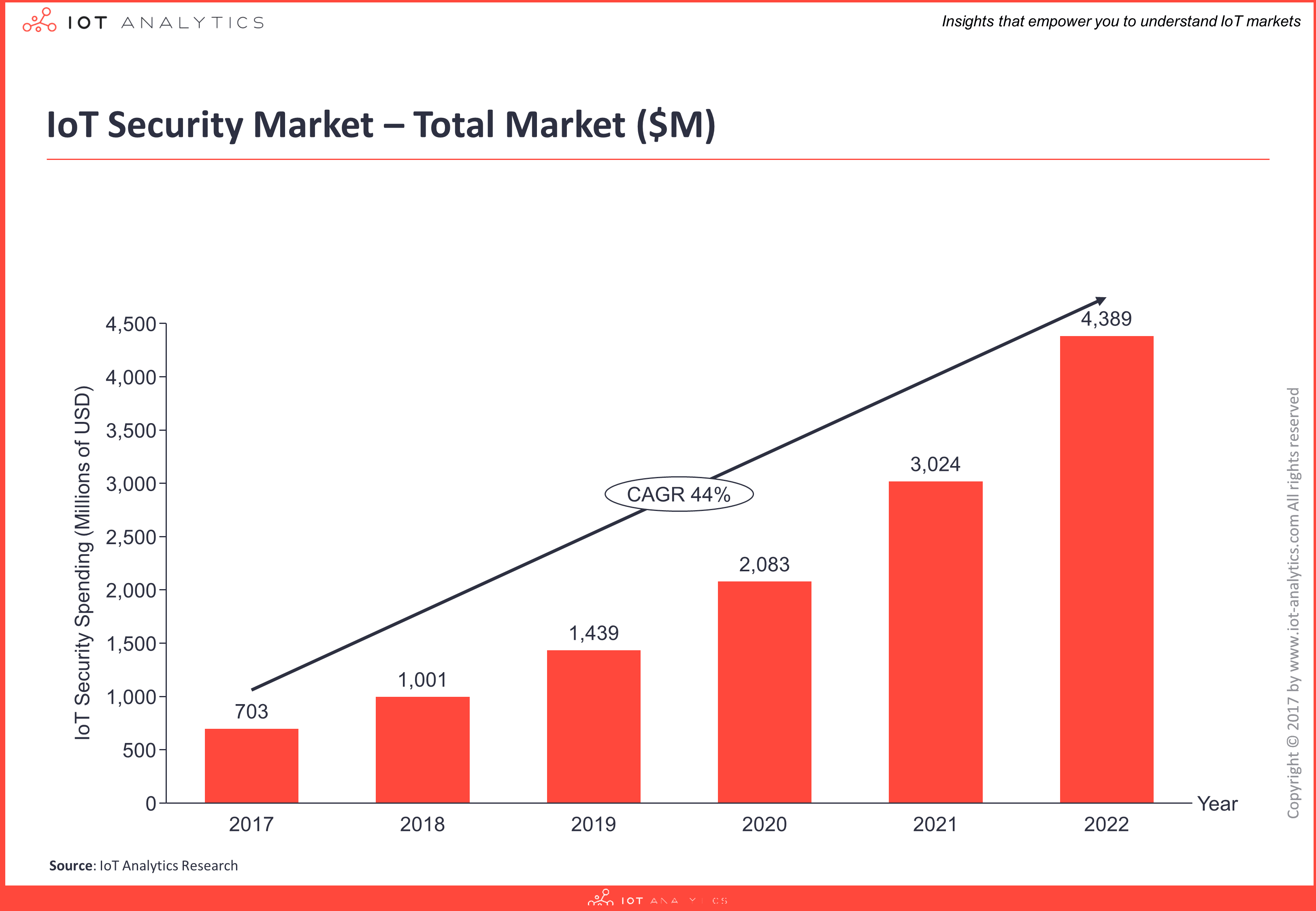
IoT security spending is currently estimated at $703M for 2017 and the fast growing market (CAGR of 44%) is forecast to become almost a $4.4B opportunity by 2022.
The report breaks down the IoT security market by segment, showing current and expected spending for IoT security solutions in greater detail across 12 specific industries:
B2C – Smart Home, B2C – Wearables & other consumer IoT, Connected Car, Connected Health, Energy / Utilities, Gov. / Military / Public Services, Industrial / Manufacturing, Retail, Smart cities, Supply Chain, Transportation (non-car), and Other.
The IoT security market is an aggregation of innovative startups and established firms such as global chip manufacturers, infrastructure providers, as well as cloud and enterprise software companies. Cisco is the current market leader in the fragmented IoT security market with an estimated market share of 7%. The top 10 providers account for over 40% of the IoT security market.
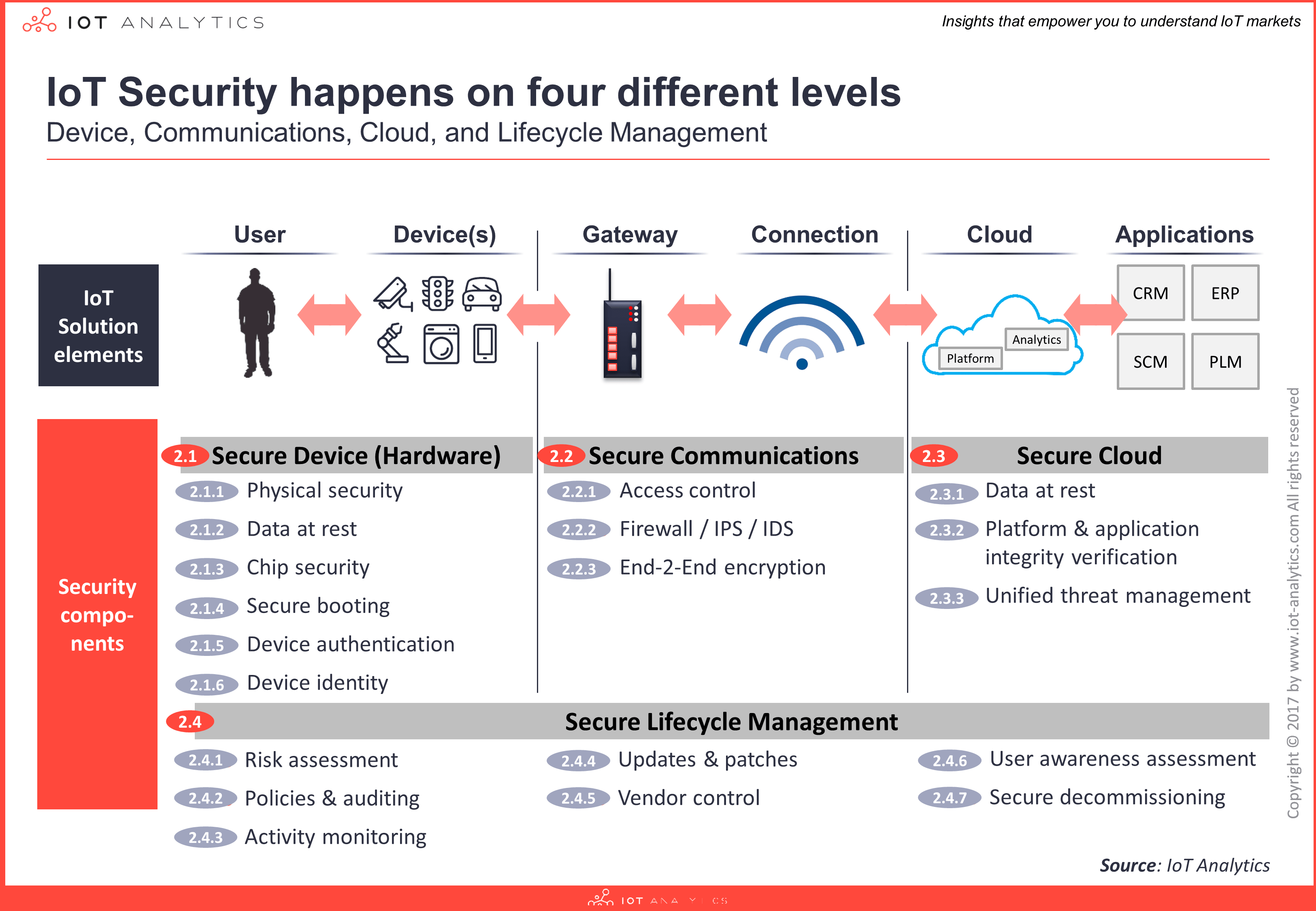
An extensive segmentation breaks down IoT security into 4 layers (device, communication, cloud, and lifecycle management) and 21 technology areas (including Services and Other) as in the exhibit below. Furthermore, the report presents a comprehensive history of cyber security viruses (IT), cyber physical attacks (OT) and IoT attacks from over 60 security breaches and provides a deep-dive into 8 specific IoT security solution implementations currently in the market.
In addition, to better understand the market players the report includes detailed profiles of 10 large IoT security providers and 5 innovative smaller firms as well as a comprehensive database classifying 150 companies in the field. The report also describes the top 6 trends and main challenges affecting IoT security.
For a detailed overview of the contents, see the additional Table of contents tab above.
Selected companies from the report:
ARM, Atmel, Airbus Defence, Barracuda, Bastille Networks, Bayshore Networks, Cisco, ClearBlade, Comarch Technologies, Darktrace, Digicert, Device Authority, Dell, Endian, Forescout Technologies, Fortinet, Gemalto, HPE, IBM, Infineon Technologies, Intel, Juniper, Kaspersky Labs, Lightcyber, McAfee, Microsoft, Mocana, NXP, Palo Alto, Risucre, Rohde & Schwarz, SAP, Symantec, Thales e-Security, Utimaco, Venafi, WISeKey, Wurldtech (GE), ZingBox
Request Sample:
Request a sample of the market report and market model data: