In short
- Covid-19 is leading to a surge in IT, OT and IoT security adoption.
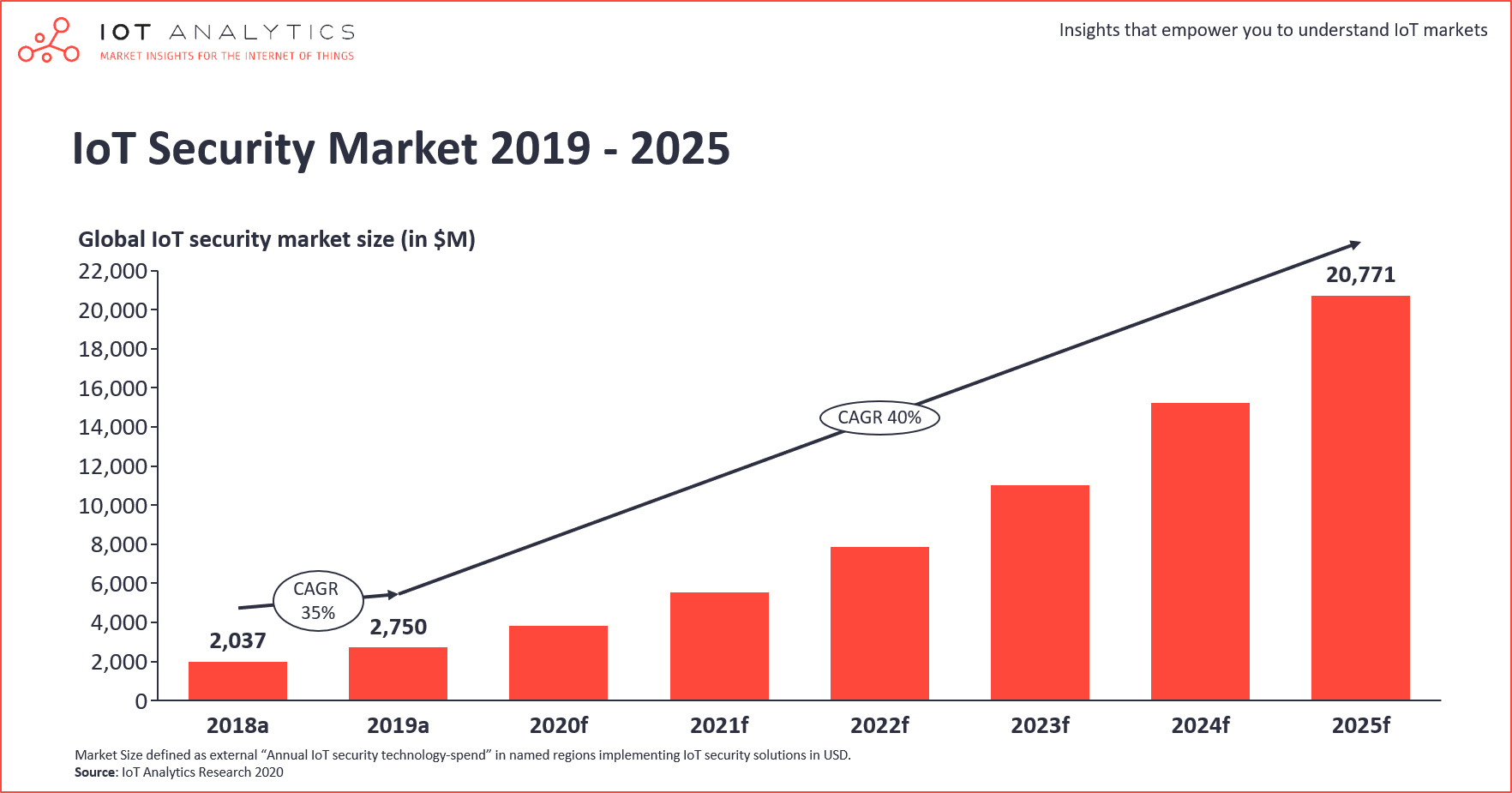
- IoT Analytics published a comprehensive 123-page report detailing the $2.8B IoT Security market (2019), including current trends, technologies, and competitive landscape.
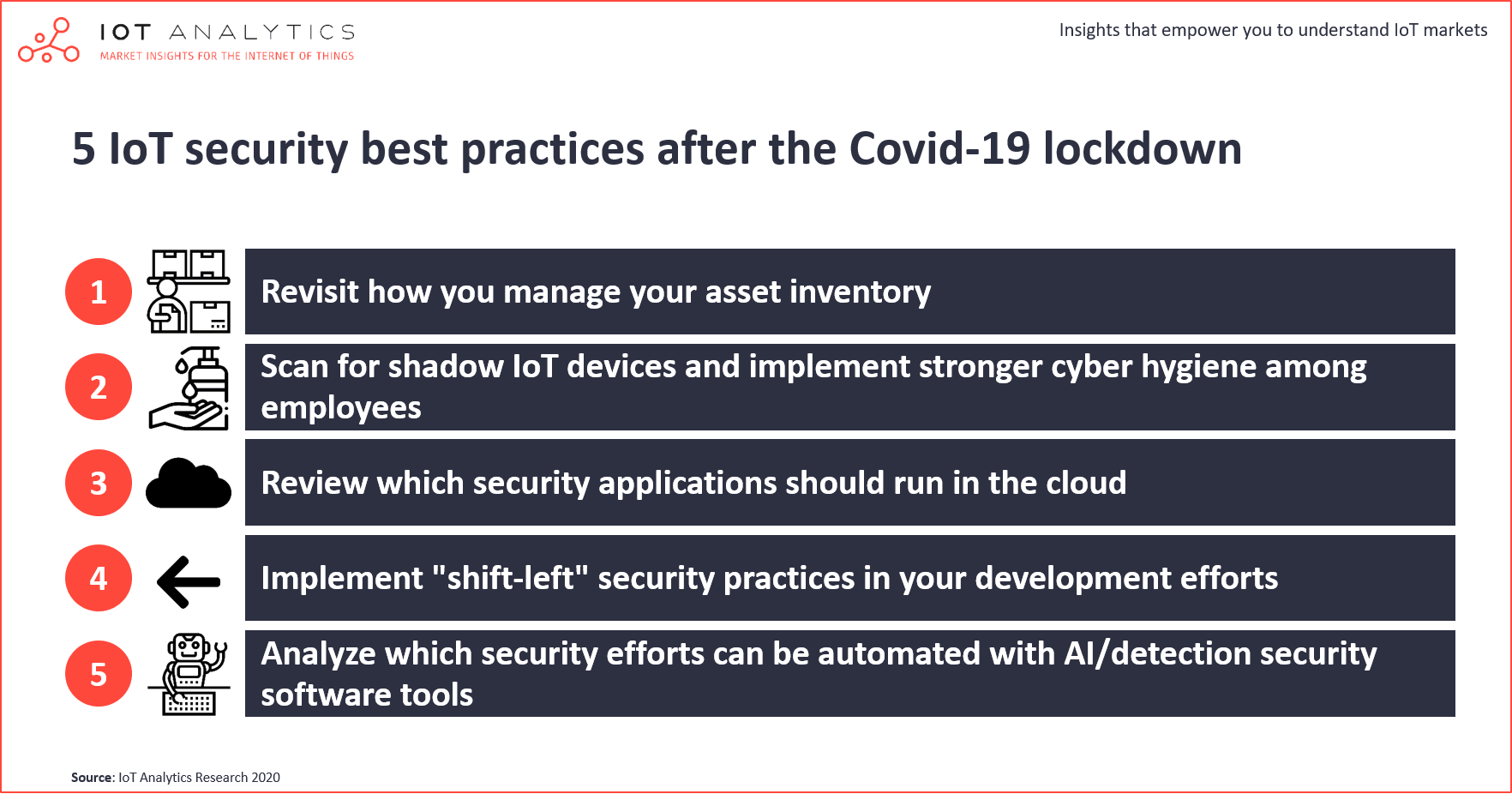
- IoT Analytics suggests for organizations to particularly look at 5 IoT Security best practices after the Covid-19 lockdown: 1. Managing the asset inventory 2. Scanning for shadow IoT devices 3. Reviewing cloud security 4. Implementing “shift-left” security practices 5. Integrating security automation and AI.
Why it matters
- Covid-19 has led to an increase in new cyber attacks
- Corporate boards are asking their engineering, OT, and IT departments to improve and review their cybersecurity setup. Technology vendors and users alike should educate themselves on the new reality now.
Covid-19 is leading to an acceleration in worldwide cybersecurity adoption
While almost all industries and many technologies have experienced a drop in demand in the first months of 2020, the opposite is happening in the cybersecurity industry: demand is increasing. On May 21, 2020, one of the leading cybersecurity vendors, Palo Alto Networks, raised Q4 2020 revenue guidance. CEO Nikesh Arora said that in his view Covid-19 has led to an explosion of the attack surface and he believes “Covid-19 accelerated the [security] trends in the direction of integration, consolidation, and cloud transformation”.
“Covid-19 accelerated the [security] trends in the direction of integration, consolidation, and cloud transformation”.
Nikesh Arora, CEO at Palo Alto Networks
IoT Analytics already reported in April 2020 in the article titled “The impact of Covid-19 on IoT” how cyberattacks in general had increased throughout the first months of the Covid-19 crisis, and how it raised the importance of IoT security in light of the changing threat landscape.
This week, IoT Analytics published an in-depth 123-page market research report titled “IoT security market report 2020-2025” which sizes and analyzes the $2.8B IoT security market (2019) in detail. For clarification: IoT security refers to the portion of the global cybersecurity market that deals with securing connected consumer and enterprise IoT devices that reside in (often cloud)-connected environments.
(Note: Pure on-premise/local networks as well as pure IT application and IT infrastructure security solutions are not classified as IoT).
Among other things the report looks at 20+ current IoT security trends and a number of other areas of interest such as cloud-based IoT security. This article highlights 5 of these areas that are particularly important for companies as they come back from the Covid-19 lockdown and look to secure their IoT devices and assets:
IoT security best practice 1: Revisit how you manage your asset inventory
As CEOs ask their IT, OT and engineering departments to review corporate security strategies in light of the Covid-19 lockdown, one of the immediate priorities is to ensure that the organization has a decent overview of their inventory of assets and IoT devices. Unfortunately, this overview is often incomplete and only available on a high level. The restart after Covid-19 presents a unique opportunity to build a holistic asset inventory with a much deeper knowledge of individual assets. It will prove invaluable for all other security initiatives that follow.
A proper asset inventory should provide answers to 4 key questions:
- What assets do I have? A list of all assets including their hardware and software specs is the basis of any asset inventory.
- What are the typical traffic patterns of my existing assets? An analysis of the typical network traffic between devices is the basis for observing abnormalities (i.e., potential attacks) and allows for running software tools for automated threat detection/response.
- How updated are my assets? Lifecycle management becomes easier when an enterprise keeps track of all updates and patches.
- How fast can we react in case of an attack? Cyber- as well as physical attacks on an asset require a rapid response. The longer it takes to locate and to fix an asset, the higher the costs for the organization. The director of security services at a major industrial conglomerate shared this with IoT Analytics:
“Once, we detected a vulnerability at some asset with a size of a matchbox, which is located somewhere at a huge industrial facility. An automation engineer was very upset, as he could not find it. I cannot stress enough the important of knowing your assets.”
Without a proper asset inventory, implementing a decent security strategy is like “trying to grow a harvest without knowing what crops you planted.”
IoT security best practice 2: Scan for shadow IoT devices and implement stronger cyber hygiene among employees
The millions of employees working from home during the Covid-19 crisis have brought to light a new security issue: “Shadow IoT devices”. Shadow IoT refers to employees bringing unauthorized devices into the enterprise. These devices present a significant source of vulnerability at every organization, because they increase the attack surface by giving access to an enterprise network, while having little security measures.
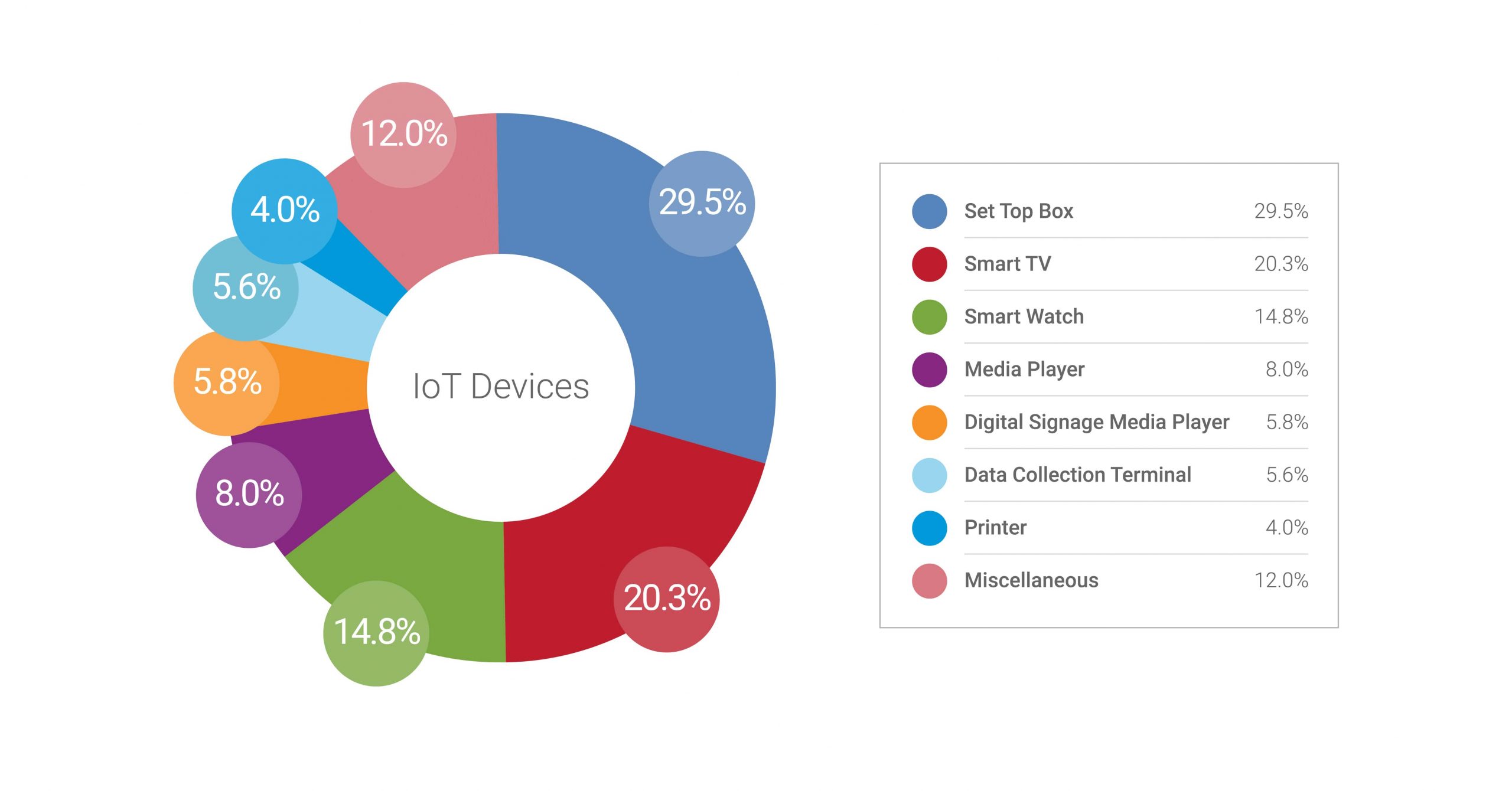
In February 2020, ZScaler, a leading cloud security provider, announced that they tracked a 1,500 percent increase in IoT devices usage increase at enterprises. The biggest categories of unauthorized IoT devices that Zscaler observed include digital home assistants, TV set-top boxes, IP cameras, smart home devices, smart TVs, smart watches, and even automotive multimedia systems. Each asset can be used as a point of exposure to get access to an enterprise network.
IT and security professionals at enterprises should pay more attention to this phenomenon and double down on educating employees about the security hygiene practices. They should design security trainings with the goal to minimize the risk from employee action, such as an unintentional negligence, privacy violation, or insider threat. Numerous vendors, both SMEs and big enterprises, increasingly provide a “security awareness training”, which aims to provide employee trainings and to consult on the risk management.
IoT security best practice 3: Review which security applications should run in the cloud
Companies that had migrated some of their tools and applications from an “on-premise” setup to the cloud before the Corona pandemic struck found it easier to manage these remotely.
As a result, many technology executives and experts believe that a massive wave of cloud adoption is on its way post Covid-19. Cloud security will be part of that wave as security tools share many benefits with other cloud-hosted applications such as the ability to scale to new assets quickly, apply software patches remotely, and integrate with other tools easily through standardized APIs. At the same time, cloud connections can significantly increase the risk of exposure or data breaches because they open up a closed-loop system to allow access from the outside by connecting to the cloud.
Now is the time for IT, Security, and Operations departments to revisit which existing security applications may need to migrate to the cloud. Not less importantly, they should revisit which ones should come back on-premise, with a thorough risk assessment. Security software tools that are currently enjoying traction in the cloud include intrusion detection/prevention systems (IDS/IPS), security information and event management (SIEM), and virtual firewalls.
IoT security best practice 4: Implement “shift-left” security practices in your development efforts
Until recently, security and software development were two different areas of practice. This separation has proven over time to lead to an increase in security vulnerabilities. In the last 5 years, the so-called “shift left” security approach has gained popularity. “Shift-left” refers to the practice of moving security to the earliest possible point in the software development process. It is leading to the DevOps process transforming into something known as DevSecOps. In DevSecOps, collaboration is key: security professionals work closely with the rest of the DevOps team to minimize potential hazards.
As Covid-19 lifts security to one of the main corporate digital initiatives, the implementation of shift-left in the development teams should be closely examined.
The shift-left approach can lead to large savings. The System Sciences Institute at IBM found that addressing security issues in design was six times cheaper than during implementation. The same study also found that addressing security issues during testing could be 15 times costlier. As the number as well the nature of security attacks worsened with the Covid-19 crisis, the shift-left security concept is now becoming a best practice.
IoT security best practice 5: Analyze which security efforts can be automated with AI/detection security software tools.
With the ongoing rapid development of AI, several traditional security solutions are being supplemented by Machine Learning capabilities to deliver better and often faster outcome. Many of the product announcements of security vendors in the last months relate to AI-based security tools, such as Cisco’s recent introduction of AI network analytics. Security professionals should consider these new tools as they pave the way to moving from strict security prevention to a detection strategy.
One area of interest is machine learning-enabled anomaly detection for threat detection. Algorithms constantly run through IoT device traffic data to detect abnormal behavior. An instant notification is generated in case something is off. Applications can be programmed to automatically trigger reaction to specific abnormalities – this feature is helpful when rapid response is needed.
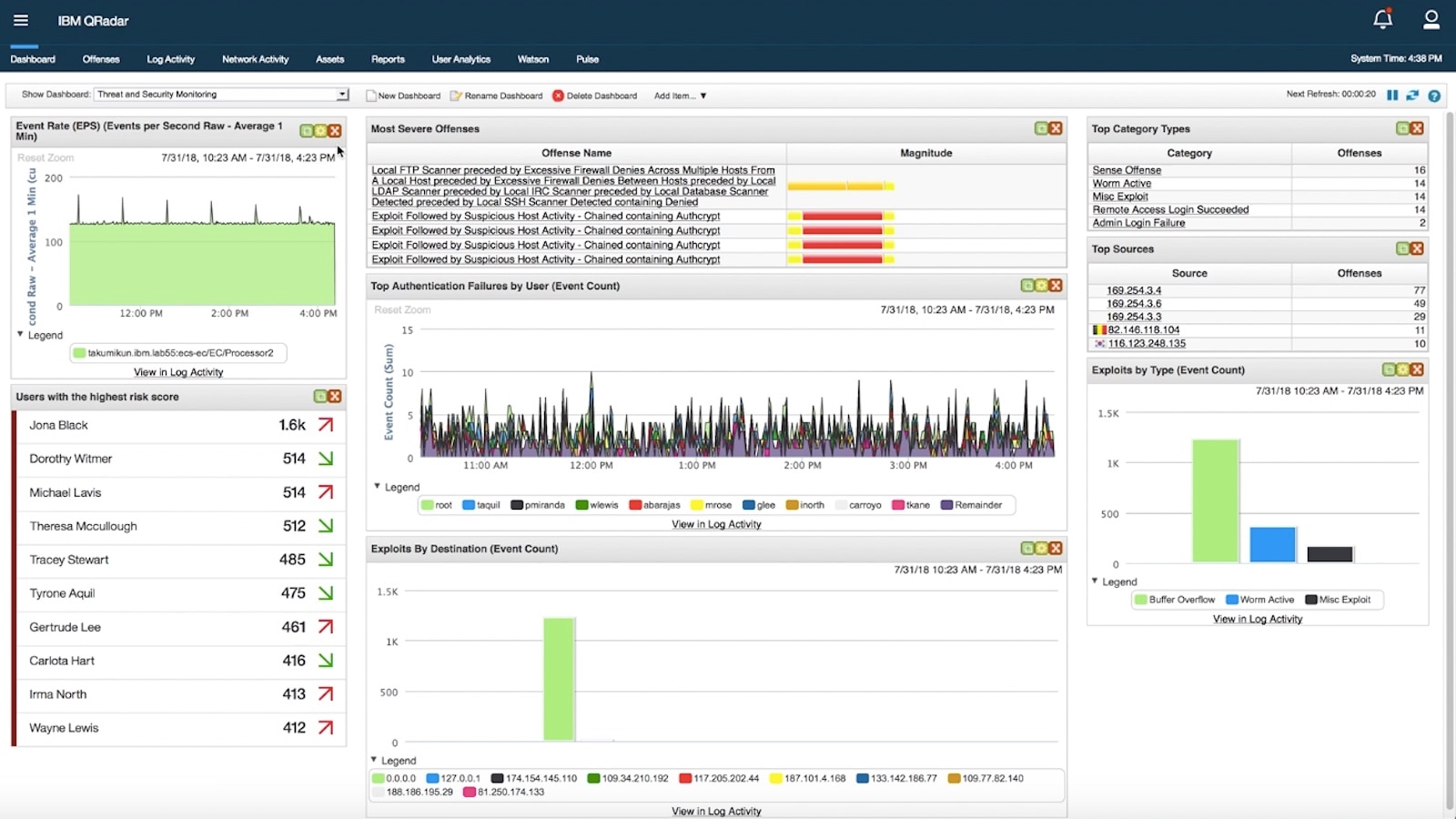
Another area that is witnessing AI-enhancement is traditional Security Information & Event Management (SIEM) solutions. They are nowadays often supplemented by analytics capabilities to provide streaming data analysis and threat modelling. An example of such solution is IBM Qradar.
More information and further reading
Interested in learning more about IoT security?
The 123-page IoT Security Market Report 2020-2025 is part of IoT Analytics’ ongoing coverage of IoT Software, Services and Hardware and includes many additional insights not discussed in this article. The main purpose of the report is to help our readers understand the current IoT security landscape by defining and analyzing the market.
This report provides answers to the following questions (among others):
- What is IoT Security (a definition)?
- How is IoT Security different from traditional IT Security and OT Security?
- Which IoT technology companies are OEMs partnering with to build IoT Security solutions?
- What is the market size and forecast for IoT Security solutions?
- How does the market break down by security type, industry, and geography?
- What are the main trends & developments shaping the IoT Security market?
- What are the key IoT Security threats and what frameworks are used to measure a security risk?
- How is Covid-19 affecting the IoT Security market?
- What is the end-user view of IoT Security in terms of adoption, ROI, and budgeting?
A sample of the report can be downloaded here:
Are you interested in continued IoT coverage and updates?
Subscribe to our newsletter and follow us on LinkedIn and Twitter to stay up-to-date on the latest trends shaping the IoT markets. For complete enterprise IoT coverage with access to all of IoT Analytics’ paid content & reports including dedicated analyst time check out Enterprise subscription.